In this post I’ll be performing OS Injection using commix on an intentionally vulnerable machine BWAPP !!!
I’ll be performing this attack on Kali Linux against an intentionally vulnerable application bWAPP(buggy web application) !
For downloading and setting up bWAPP on your Kali Machine, check out the article below for the entire procedure :-
https://www.kalilinux.in/2020/02/bwapp-in-kali-linux-2020.html
Once you are done with the complete setup , we are set to HACK IT !!!
What is OS command injection?
An OS command injection is a web security vulnerability that enables the execution of unauthorized operating system commands. An OS command injection vulnerability arises when a web application sends unsanitized, unfiltered system commands to be executed. Due to the insufficient input validation an attacker could inject their own commands to be operated on the shell level. The attacker introduces operating system commands via user- supplied data such as cookies, forms or HTTP headers.
What is Commix💉?
Commix is a Automated All-in-One OS Command Injection Exploitation Tool
Commix (short for [comm]and [i]njection e[x]ploiter) is an open source penetration testing tool, written by Anastasios Stasinopoulos (@ancst), that automates the detection and exploitation of command injection vulnerabilities.
Automates the detection and exploitation of command injection vulnerabilities in certain vulnerable parameter(s) and/or HTTP header(s).It comes pre installed with Kali Linux.
Open up your Kali terminal and enter the below commands if you have uploaded your bWAPP on the apache server :-
sudo service apache2 start
sudo service mysql start
Then head on to your browser and locate to ” localhost/bWAPP/login.php “

Then select OS Command Injection and hit the HACK button as shown above !

This is a page where we can do dns lookups of any website.
So,now simply click on the the LOOKUP button.
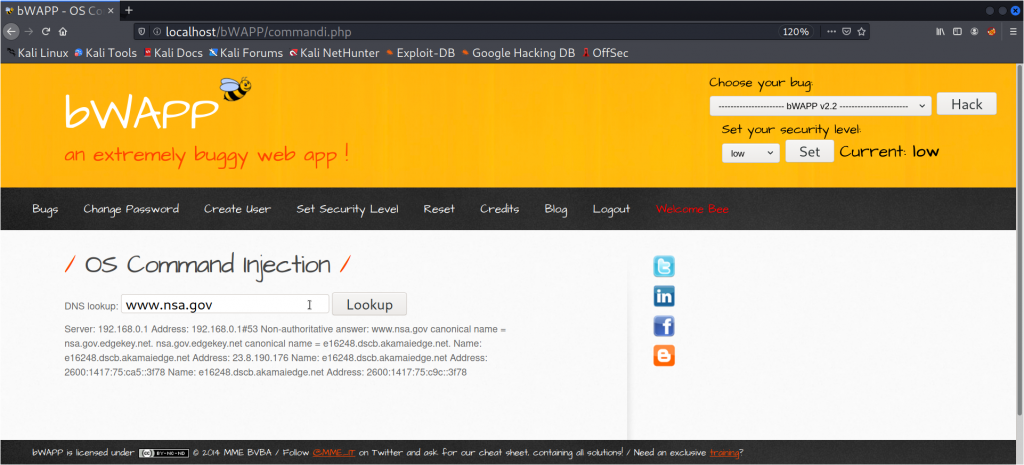
This is how a dns lookup looks like 👆
But now, we need to check whether this dns lookup search parameter is vulnerable to Operating System Injection.
To do that we can add a semicolon ( ; ) and try to execute any OS command like pwd,whoami,ls or any other.
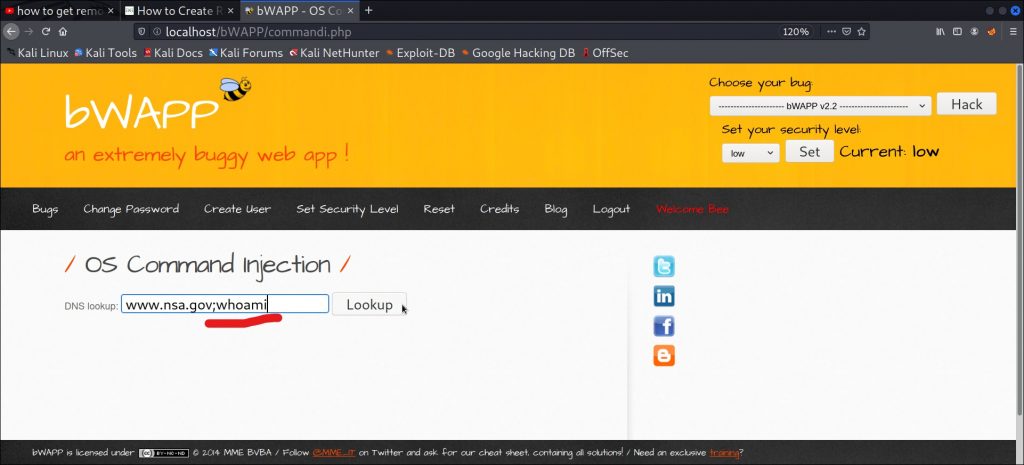
Here I have added ;whoami at the end.
Now hit ENTER.
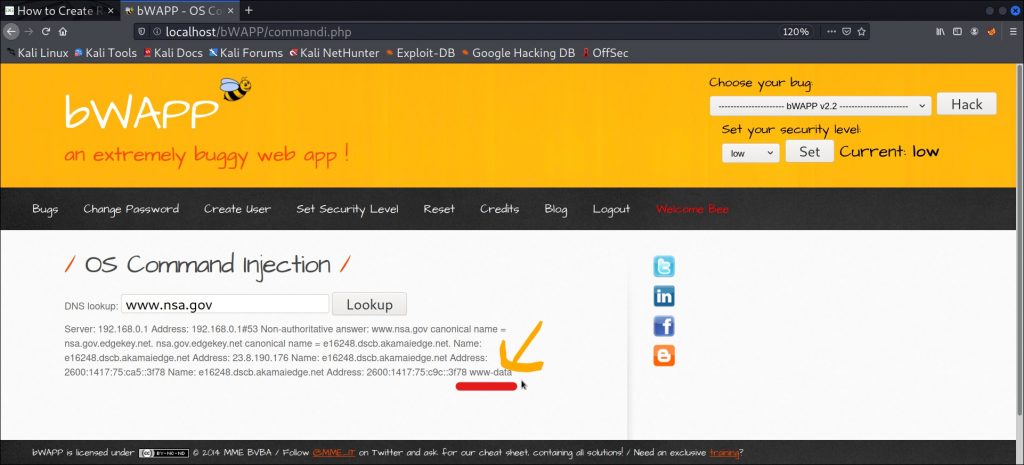
Here , in the above image you can see that in the response we have www-data
This happened since we added a query (;whoami) at the end which got reflected in the result;
Which means that this is vulnerable to OS Injection.
Since our goal this time is to exploit the OS Injection vulnerability with an automated tool called commix, we need to first create a text file which contains the intercepted file of the dns lookup
So fire up the BurpSuite with the following command on your terminal :
burpsuite &
For configuring Burpsuite with your browser, check out the below link:-
https://portswigger.net/burp/documentation/desktop/external-browser-config/browser-config-firefox

Make sure the intercept is also on !! as shown above.
Then head back to the browser and hit the LOOKUP button again as shown below.
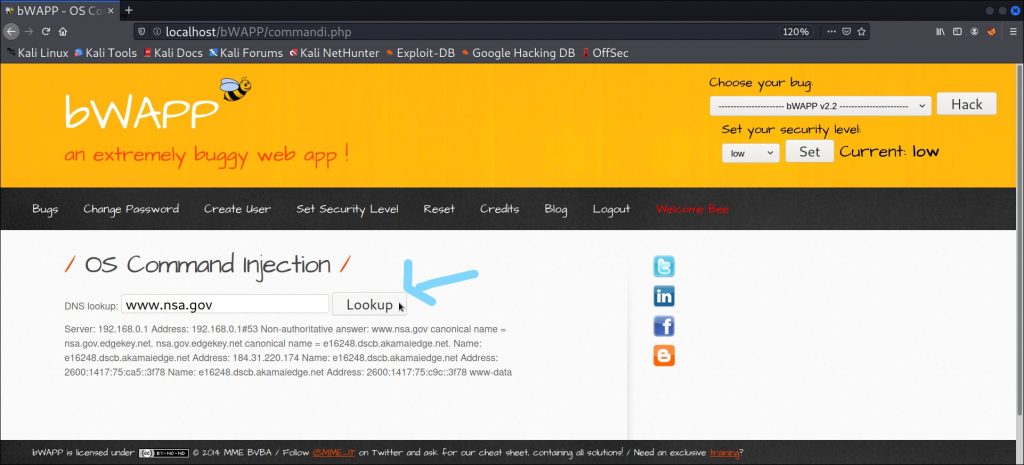
As soon as you do that, your request will be intercepted , have a look at the Burpsuite now.

Now copy the entire highlighted part and move back to your terminal.

Here I have changed my directory to /usr/share/commix and there I’m creating a file named “osinject.txt” (you can name it anything)
and inside that file I’m gonna paste the entire intercepted part I copied from Burpsuite as shown below.
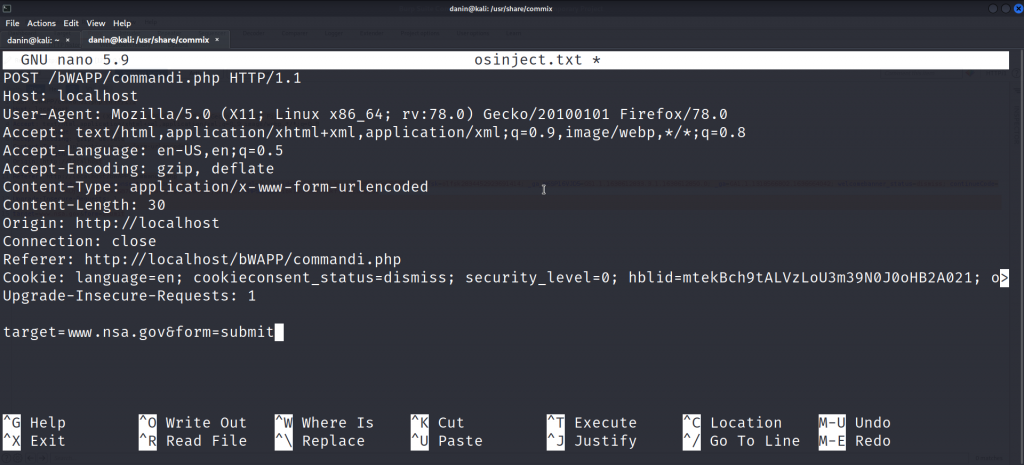
Once this is done press ctrl+x to and then enter Y to save the text file.
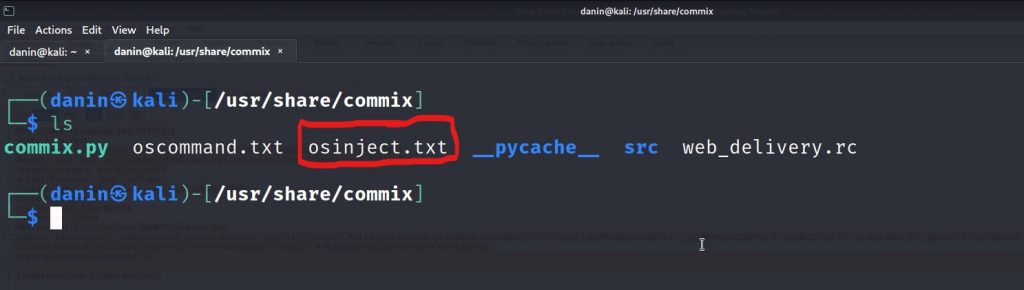
Now when we type “ls” we can see the osinject.txt file present over there!
Now the final step :-
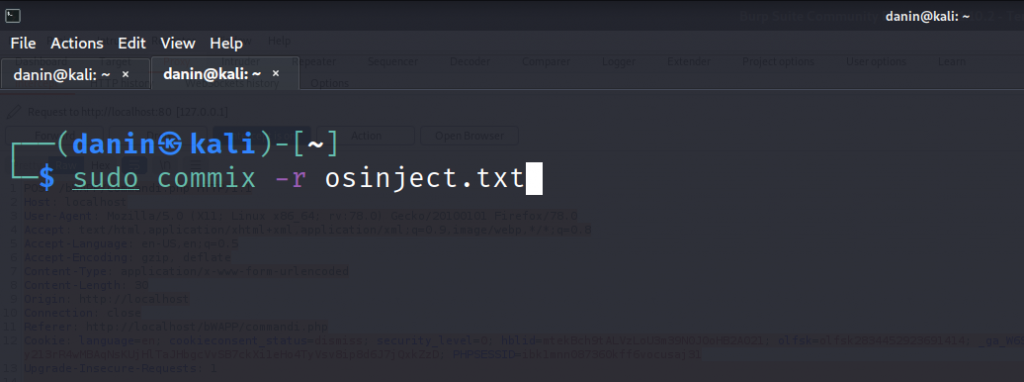
sudo commix -r osinject.txt
Here we are using commix and providing it the intercepted file to perform an automated OS Injection attack against it!!!

The process has been initiated and it might take a few minutes. (BE PATIENT)

Now it’s asking whether we want a pseudo-terminal shell…..Press Y
And as soon you do that…….

BOOOM ⚡⚡⚡you have a shell…..basically you have exploited the OS Injection vulnerability and took control over it!!!
But do you want to take this to another level to perform more severe attacks???
Head on to the next page where I’ll be converting this general shell into a Meterpreter shell !!!
Isn’t it interesting???
So what are you waiting for?
HEAD ON
